SOCKS proxy via SSH
Posted on June 16, 2022 • 5 minutes • 857 words • Other languages: Français
In this article, I will introduce you to the concept of proxy and its uses. Then I will show you a simple method to set up a SOCKS proxy through an SSH tunnel. This article is not intended to anonymize an internet connection. The goal here is to access another network to bypass the limits of a firewall or to access services, web interfaces… available on this other network.
What is a proxy ?
Proxy means agent, so it’s a server (in other words another machine) to which you will send data and to which you give “mandate” to route these data.
This means that you must have absolute confidence in the proxy server you use.
If you use a corporate or school filtering proxy for example, all your browsing data can be read, be aware of that. If you want to use an “anonymizing” public/open proxy (never do that…) it’s the same thing.
The utility of a proxy
There are many uses for a proxy but I will stop at 4 uses that I consider to be the main ones:
- The filtering proxy : mainly used in companies and schools, it allows to apply filtering rules limiting access to certain URLs for example.
- The bypassing proxy whose objective is the opposite of the previous one. The proxy is used as an intermediary, it is located on another network (another country, at home, in a DC…) and will not be affected by the filtering rules in place on the network where you are physically present.
- The anonymizing proxy. I don’t like this term very much because in reality a simple proxy can be easily “remounted”. For this specific use of a proxy, one should preferably use a chain of several proxies (a bit like TOR and one should couple this method with VPN for example. But this is not the subject of my article.
- The reverse proxy which is a very particular application. Generally placed in front of a web server, it allows users to access servers of an internal and private network in all transparency (hence the notion of reverse proxy). HTTP reverse proxy servers (NGINX, APACHE…) are a crucial link for load-balancing (HAProxy) or even for container-based micro-services architectures (Docker…).
SOCKS proxy via SSH server
Having said that, let’s get a little technical and get back to what we’re interested in today: implementing a SOCKS proxy through an SSH tunnel!
Just as creating an SSH tunnel is done with the simple -L option in SSH, starting an SSH SOCKS proxy just requires the -D option. The latter enables the dynamic forwarding feature of SSH which supports the SOCKS4 and SOCKS5 protocols.
With this -D option and a browser setting (see below), your SSH connection will be a true SOCKS proxy! It will allow your web browser to dialog through an encrypted SSH tunnel to the remote SSH server’s network card as if it were its own.
This means that all web resources accessible to the remote server will now be accessible to your browser. As if you were present on the network. And your identity for the visited sites will be the one of the remote server too (do the test by visiting monip.io after configuration!)
Come on, you can’t stand it anymore and the CTRL+C is itching you, so here is a simple example of a command to copy and run :
ssh user@REMOTE_HOST -D 8080
- The port (here 8080) is free
- Use the
-foption of SSH if you want to put the command in background
Then, in your browser, go to the network settings in order to activate the SOCKS server by filling in the port selected. Example here for Mozilla Firefox:
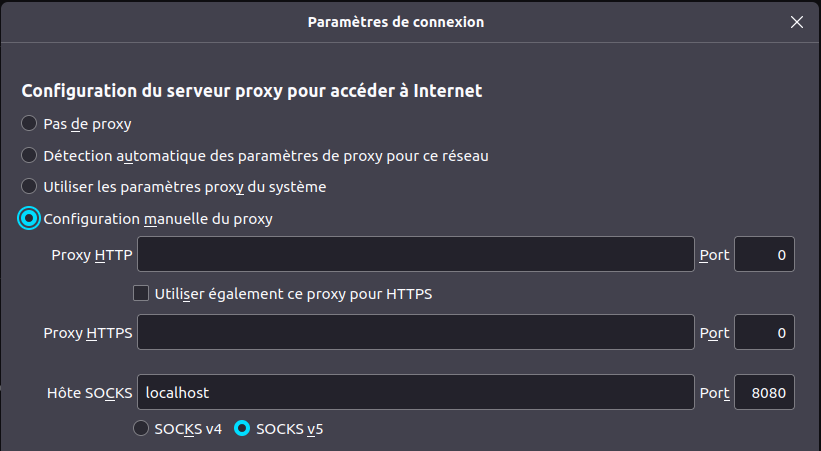
That’s it ! Now access any WEB interface present on the LAN of the remote server via your browser.
Bonus
You all remember the good old OSI model, right ? As a reminder, here it is:
A proxy is applicative, so it acts at the layer 7 application level. VPN protocols, for example, generally act much lower, on Layer 3 Network (or even Layer 2). So there is no point in looking for a proxy with network commands such as `traceroute’, you won’t see it.
So to configure a proxy or check that there is one in place on the machine you are using, it is done :
- at the level of your OS
- at the level of your web browser
- at the level of an SSH client
- … In short, it’s done at the application level. Remember this 👍
Go further …
I strongly recommend that you complete this reading by watching the video of the excellent Yves Rougy and that I discovered while writing my article. You will find it here ! (French content)
He also shows you how to set up a SOCKS proxy but he mostly talks about SSH tunneling if you are interested and he even explains perfectly the `-R’ option, not easy to understand. In short, go for it!